

Netskope decodes traffic across the cloud to understand content and context in real-time across thousands of apps.
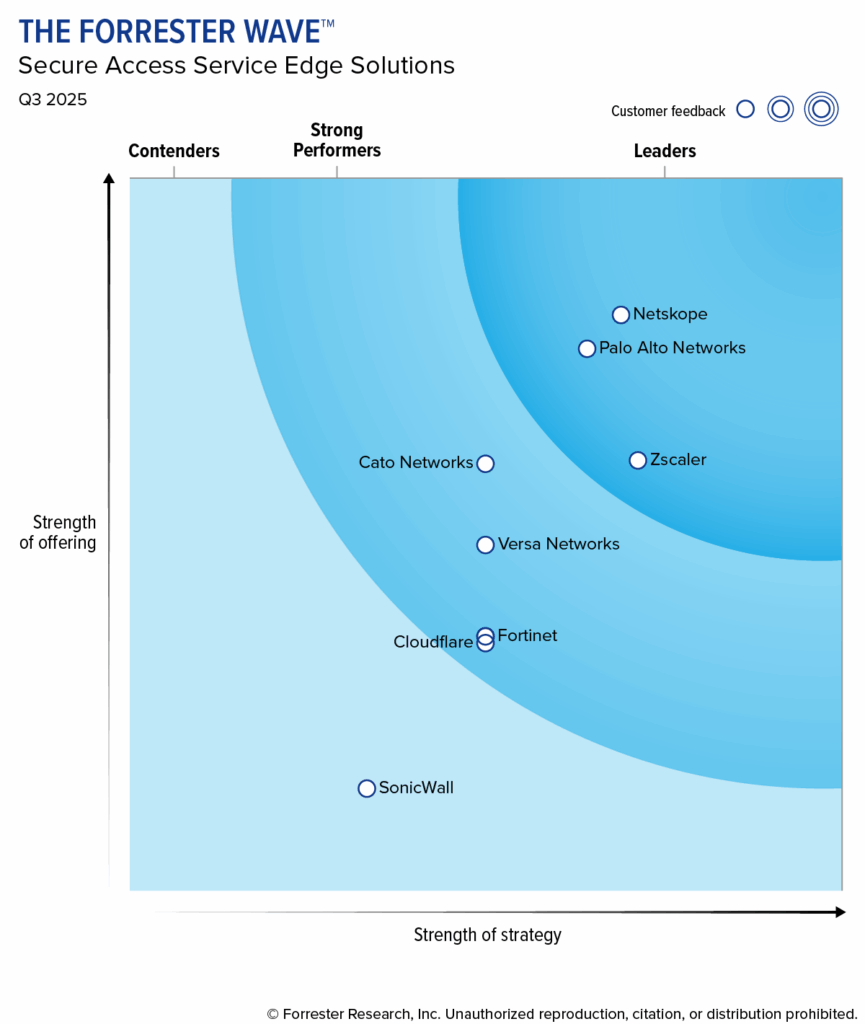
Netskope is a Leader in The Forrester Wave™ for Secure Access Service Edge
Lock it down.


Netskope inspects web traffic and cloud services with deep context understanding, analyzing transactions in real-time.
Transaction event streaming and user risk scoring enables adaptive access policies based on context in use.

Frequently Asked Questions
SASE distributed cloud architecture eliminates single points of failure that cause network outages. Automatic failover capabilities route traffic through multiple connection paths when primary links experience issues. Global load balancing distributes traffic across regional points of presence for optimal performance and uptime. Security functions remain active even during infrastructure disruptions. Our Tampa-based monitoring team receives instant alerts for any performance degradation. Our Zero Trust implementation leverages redundant SASE infrastructure for maximum business continuity.
Leading SASE platforms analyze five critical dimensions through context-aware engines: user identity and risk score, device posture and management status, location and time context, application type and sensitivity, and data classification and handling requirements. This multi-dimensional analysis enables nuanced decisions like allowing document access while blocking downloads, permitting read-only access from unmanaged devices, or requiring additional authentication for sensitive data access. Traditional security makes binary allow/deny decisions; modern SASE behavioral analytics provides graduated response based on comprehensive context analysis. Our context-aware security deployment eliminates security-productivity trade-offs through intelligent policy enforcement.
Modern SASE platforms use User and Entity Behavior Analytics (UEBA) with machine learning to establish baseline behavior patterns for each user, then assign risk scores based on deviations from normal activity. The system analyzes multiple context factors: access timing, geographic location, device type, data sensitivity, and transaction patterns. For example, a sales manager downloading contact lists triggers analysis of whether this occurs during business hours, from usual locations, on managed devices, and follows typical usage patterns. Risk scores automatically recover over time when risky behavior stops, ensuring legitimate users regain full access. Our UEBA deployment provides intelligent threat detection without productivity disruption.
Security Service Edge (SSE) delivers cloud-native security including Secure Web Gateway, CASB, and Zero Trust Network Access from unified policy management. Identity-centric security follows users and devices regardless of network location. Access decisions consider user identity, device posture, application sensitivity, and behavioral patterns. Policies apply consistently whether users access resources from office networks, home connections, or mobile devices. Our Zero Trust architecture implementation integrates SSE capabilities with existing identity management systems.
SSE (Security Service Edge) represents the security component of SASE that delivers cloud-native security services including Secure Web Gateway, CASB, and Zero Trust Network Access from a unified platform. Unlike traditional security that relies on network perimeters and appliances, SSE provides identity-centric security that follows users and devices anywhere they connect. The architecture eliminates security gaps by applying consistent policies whether users access resources from the office, home, or remote locations. Our Zero Trust architecture implementation leverages SSE capabilities to provide comprehensive protection.
Advanced SASE platforms use AI-powered behavioral analytics to monitor user activity patterns and identify risky behavior before data theft occurs. The platform tracks typical user actions—like occasional file uploads to G Drive—then detects anomalies such as increased time on LinkedIn, Glassdoor, or resume sites. When behavioral risk scores drop below 600 (out of 1000), the system automatically restricts data movement capabilities without blocking legitimate work. This proactive approach prevents disgruntled employees from exfiltrating data during their departure planning phase. Our behavioral analytics implementation transforms reactive DLP into predictive data protection.
SASE platforms provide comprehensive Data Protection through integrated Data Loss Prevention (DLP) that monitors and controls sensitive data across all communication channels and cloud applications. Unlike traditional DLP solutions that require separate deployments, SASE delivers unified data protection policies that follow users regardless of location or device. The platform automatically identifies, classifies, and protects sensitive information like PII, financial data, and intellectual property through real-time scanning and policy enforcement. Our managed IT services ensure your SASE DLP policies are properly configured and continuously monitored.
SASE platforms include comprehensive Cloud Access Security Broker (CASB) capabilities that provide visibility, compliance, and threat protection for cloud applications and services. The integrated CASB monitors user activities, enforces data protection policies, and detects anomalous behavior across all sanctioned and shadow IT applications. Modern SASE solutions now incorporate Gen AI engines that enhance threat detection through behavioral analytics, automated policy recommendations, and intelligent response capabilities that adapt to emerging threats in real-time. Our managed IT platform leverages these advanced capabilities to provide military-grade protection for your cloud environment.
SASE Cloud Access Security Broker (CASB) monitors all cloud application usage including shadow IT and personal accounts. User activity analysis detects anomalous behavior like unusual download volumes or after-hours access. Data protection policies prevent sensitive information from leaving approved channels. AI-powered analytics identify potential insider threats and account compromise before data loss occurs. Real-time alerts enable immediate response to suspicious activities. Our SASE platform provides 24/7 monitoring of all cloud application interactions.
SASE (Secure Access Service Edge) is a cloud-delivered security and networking architecture that merges SD-WAN with comprehensive security functions like Secure Web Gateway, CASB, and Zero Trust Network Access into a single platform. Unlike traditional approaches that route traffic through data centers, SASE provides direct cloud connectivity with consistent security policies across all users and locations. This modern cloud network architecture eliminates the complexity of managing multiple point solutions while delivering enhanced performance and security. Our cloud infrastructure migration services can help you transition to a SASE-enabled architecture.
SASE includes comprehensive threat protection through integrated Secure Web Gateway (SWG) with real-time malware detection, URL filtering, and zero-day protection. Behavioral analytics identify advanced persistent threats (APTs) and insider risks through user activity monitoring. Machine learning-driven threat intelligence adapts to emerging attacks automatically. Sandboxing capabilities detonate suspicious files in isolated environments. Our managed IT security services configure these capabilities to prevent breaches before they impact business operations.
SASE Data Loss Prevention (DLP) monitors all communication channels from a single policy engine. Content inspection identifies sensitive information like credit card numbers, social security numbers, and proprietary data regardless of format or location. Policies follow users across devices and applications automatically. Real-time scanning prevents data transmission through unauthorized channels. Classification happens automatically using machine learning and regex patterns. Our managed IT services configure DLP policies that balance security requirements with user productivity.
Ridge IT's pre-configured banking deployments enable enterprise SASE implementation in 60-90 days versus 12+ months for traditional solutions. We leverage APIs and scripted configurations based on extensive banking experience, including FIS Horizon integration patterns and industry-specific policies. Our approach deploys baseline security immediately, then fine-tunes organization-specific requirements. The Texas bank we recently deployed was fully operational within 30 days because we eliminated the learning curve through proven automation and banking-specific templates. Our rapid deployment specialists minimize time-to-protection through proven methodologies.
SASE dramatically improves network resilience through its distributed cloud architecture that eliminates single points of failure common in traditional hub-and-spoke networks. The platform provides automatic failover capabilities, global load balancing, and multiple connection paths that ensure continuous connectivity even during outages or performance degradation. This resilience extends to security functions, maintaining protection even if individual components experience issues, while providing consistent performance regardless of user location or network conditions. Our Zero Trust implementation leverages SASE's distributed architecture for maximum uptime.
Remote Browser Isolation (RBI) within SASE platforms provides the ultimate protection by executing web content in isolated cloud environments, completely separated from user devices and corporate networks. This approach prevents malware, zero-day exploits, and advanced persistent threats from reaching endpoints by containing all web-based risks in disposable virtual browsers. When blocking threats becomes critical, RBI ensures that even if malicious content is encountered, it cannot impact the user's device or gain access to corporate resources. Our managed IT security services implement RBI as part of a comprehensive security strategy.
SASE transforms Web SaaS and Private Application access by providing direct, secure connectivity without routing traffic through traditional data centers or VPNs. The platform delivers consistent security policies for both sanctioned and unsanctioned SaaS applications while providing seamless access to private applications through Zero Trust Network Access (ZTNA). Users experience improved performance with reduced latency while IT maintains granular control over application access, data sharing, and user activities. Our cloud infrastructure ensures your applications are properly secured within the SASE framework.
Inc. Magazine's fastest growing leader in Managed Cybersecurity—3 years in a row.
Rapid response times, with around the clock IT support, from Inc. Magazine’s #1 MSSP.
Rapid response times, with around the clock IT support, from Inc. Magazine’s #1 MSSP.