CMMC Compliance
A Definitive Guide to the 2025 Deadline
Updated: September 10, 2025
Military-grade compliance isn’t just a catchphrase – it’s a requirement. By 2025, defense contractors will need Cybersecurity Maturity Model Certification (CMMC) to work with the Department of Defense.
Breaking News: CMMC 2.0 Final Rule Published
The Department of Defense published the final DFARS rule on September 10, 2025, officially ending months of OIRA review uncertainty. Defense contractors now have exactly 60 days until CMMC requirements begin appearing in new DoD contract solicitations on November 10, 2025.
Because it takes a few months to roll out compliance for each organization, the clock is now ticking for defense contractors to achieve compliance.
No CMMC compliance, no contracts. It’s that simple.
What is CMMC Compliance?
CMMC (Cybersecurity Maturity Model Certification) is the Department of Defense’s comprehensive framework for protecting sensitive defense information. Think of it as a military-grade security clearance for your entire IT infrastructure.
CMMC 2025 Deadline: Critical Timeline
The DoD isn’t just suggesting these changes – they’re mandating them. Here’s what you need to know:
- December 16, 2024: CMMC Final Rule took effect
- Early 2025: CMMC requirements begin appearing in contracts
- November 10, 2025: Full CMMC implementation begins
- Ongoing: Phased rollout across defense industrial base
Contract Requirements Begin
DoD contracting officers to include CMMC requirements in solicitations.
Compliance Deadline
The deadline for CMMC compliance for all MSPs, MSSPs, and other organizations that do business with DoD
Who Needs CMMC Certification?
If you’re anywhere in the defense supply chain, this affects you:
Prime Contractors
Working directly with the DoD
Sub-contractors
Supporting prime contractors
IT Service Providers
Managing defense data
Defense Manufacturers
Defense supply chain
Software Developers
Creating DoD Solutions
CMMC Checklist
Free Pre-Assessment Cheat Sheet by Ridge IT
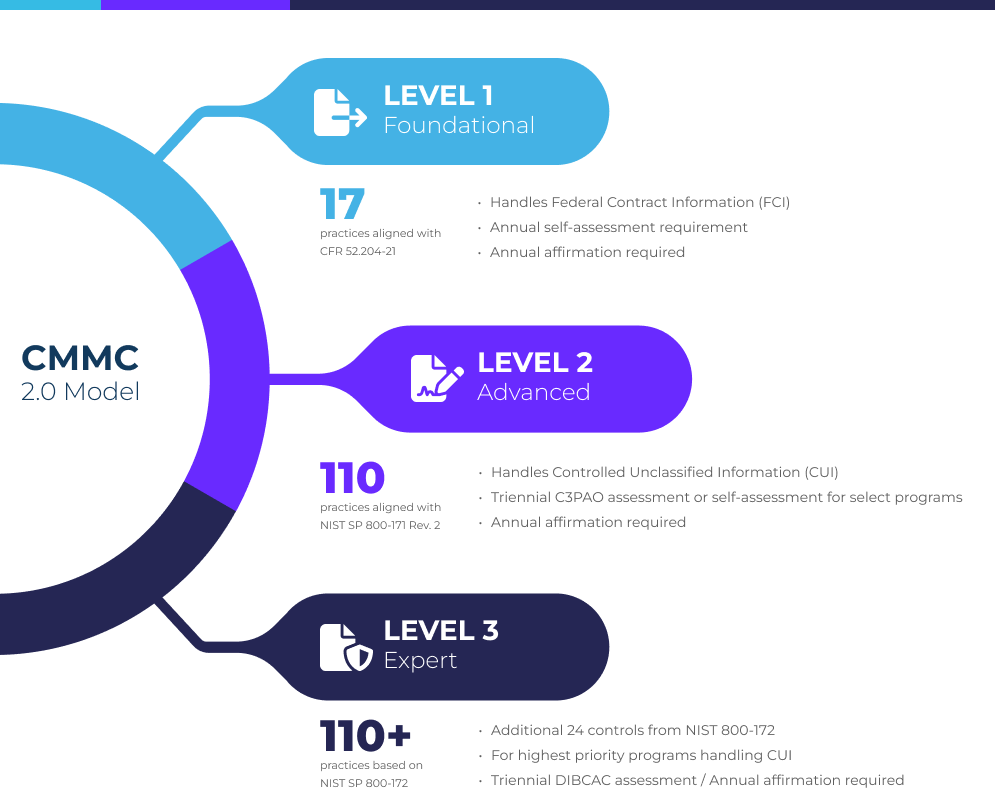
CMMC Levels
A complete breakdown of CMMC 2.0 certification levels showing practice requirements, assessments, and information handling capabilities for each tier
Key Components of CMMC:
- Federal Contract Information (FCI) protection
- Controlled Unclassified Information (CUI) safeguards
- Three distinct compliance levels based on data handling
- Third-party assessment requirements
- Regular recertification processes
The cost of making a mistake here can be the difference between your company running and being out of business. When CMMC Compliance goes in full effect, you are going to see companies go out of business because their contracts will be yanked.
Perry Schumacher
Chief Strategy Officer Tweet
How to Get CMMC Certified: Step-by-Step Guide
Determine Your Required Level
Assess your contract requirements
Review your current and upcoming DoD contracts to identify specific CMMC level requirements. Most contractors handling CUI will need Level 2 certification, while those with FCI only can qualify for Level 1.Conduct Initial Assessment
Perform gap analysis
Start with our free CMMC readiness assessment to identify critical security gaps in your current infrastructure. Our military-grade assessment framework evaluates all 110 security controls against your existing systems.Develop Compliance Roadmap
Create detailed action plan
Work with certified CMMC practitioners to build a realistic implementation timeline based on your gaps and resources. Most organizations need 12-18 months to achieve full compliance when starting from scratch.Implement Security Controls
Deploy required technologies
Begin with foundational security measures like multi-factor authentication and endpoint protection. Our Zero Trust architecture provides a proven framework for implementing CMMC controls systematically.Prepare Documentation
System Security Plan (SSP)
Document every security control, policy, and procedure in your System Security Plan. Our certified technical writers can help develop comprehensive documentation that meets DoD standards.Schedule C3PAO Assessment
Choose certified assessor
Select an authorized C3PAO with experience in your industry and certification level. Ridge IT’s military-grade assessment process includes pre-assessment readiness reviews to maximize success.Maintain Compliance
Regular security updates
Implement continuous monitoring and regular security assessments to maintain compliance. Our managed security services provide ongoing support to ensure your certification stays current.
CMMC Compliance & Implementation
Frequently Asked Questions
What CMMC mistakes should my team look for?
After hundreds of defense contractors achieve certification, we've seen how costly DIY CMMC compliance mistakes can be. The DoD found only 10-15% of self-assessed companies actually met requirements. Learn which mistakes fail certification and how to prevent them.
The most critical errors include:
- Trusting DIY assessments when CMMC deadline 2025 requires expert guidance
- Missing CUI boundary documentation that auditors require for CMMC compliance contractors
- Treating compliance like an annual event instead of continuous monitoring, which the December 16 Final Rule demands
What is the timeline for CMMC 2025?
The Department of Defense published the final DFARS rule on September 10, 2025, officially ending months of OIRA review uncertainty. Defense contractors now have exactly 60 days until CMMC requirements begin appearing in new DoD contract solicitations on November 10, 2025.
Verified Timeline Milestones:
- October 15, 2024: CMMC Final Rule published in Federal Register
- December 16, 2024: CMMC Program Rule (32 CFR Part 170) took effect
- December 16, 2024: Voluntary C3PAO assessments officially began
- September 10, 2025: CMMC Acquisition Rule (48 CFR Part 204) reviewed
- November 10, 2025: DoD contract requirements to begin
- 2025-2030: Phased rollout across entire defense industrial base
The compressed timeline creates immediate preparation urgency. Organizations need Level 2 certification before contract awards, requiring implementation of 110 security controls plus operational evidence collection. Assessment wait times already stretch 3-6 months as contractors rush toward compliance.
Smart defense contractors are starting CMMC preparation now rather than waiting for the acquisition rule publication. Early certification provides competitive advantage in prime contractor partnerships and positions organizations ahead of the compliance rush.
Navigate the complete timeline for CMMC 2025 with our detailed regulatory tracking and strategic preparation milestones.
Has the CMMC requirement date for DoD contracts changed in 2025?
(As of September 10, 2025) The cmmc requirement date for DoD contracts is November 10. 2025. Defense contractors should prepare now. Level 2 certification requires 12-18 months of preparation, and C3PAO assessment slots are filling rapidly. Waiting any longer could mean losing contracts. Our RPO Certified CMMC compliance experts can accelerate the certification process to ensure readiness regardless of when the final requirement date is announced.
What is the current status of the CMMC Title 48 rule?
The waiting is over. The Department of Defense published the final DFARS rule on September 10, 2025, officially ending months of OIRA review uncertainty. Defense contractors now have exactly 60 days until CMMC requirements begin appearing in new DoD contract solicitations on November 10, 2025.
This isn't another regulatory delay or estimate. The acquisition rule (48 CFR Part 204) is finalized, published, and will take effect November 10, 2025. If your organization handles Federal Contract Information (FCI) or Controlled Unclassified Information (CUI), the compliance countdown has officially begun.
Can organizations prepare for CMMC before the 48 CFR rule is final?
Yes, organizations can and should begin preparation immediately. The core CMMC requirements are established in the 32 CFR rule, which is already in effect. Organizations typically need significant time to implement required security controls before assessment. Voluntary certification is available, and many prime contractors are already requiring CMMC readiness from their supply chain partners.
What makes Ridge IT the #1 MSSP for DoD and government contractors?
Ridge IT delivers specialized advantages for defense contractors through certified government expertise that most MSSPs can't match. As a CMMC Registered Provider Organization, we're authorized by the Accreditation Body to provide official compliance consulting beyond typical point-in-time assessments. Our team maintains CMMC compliance ourselves for government clients, providing real-world implementation experience since supporting DIB customers for 5+ years. Our military-grade Zero Trust architecture (700+ deployments) automatically satisfies key CMMC controls while our intelligent enclave approach reduces per-user compliance costs from $60 to $20. We leverage DoD-approved technology platforms for audit familiarity, provide automated evidence documentation that CMMC auditors require, and deliver 15-minute response times with 98.7% threat prevention. Unlike general MSSPs adapting to government requirements, Ridge IT was purpose-built for mission-critical federal security from inception, this makes us the #1 MSSP for DoD.
What happens if defense contractors miss the CMMC requirement date?
When is the CMMC requirement date for defense contractors?
Defense contractors now have exactly 60 days until CMMC requirements begin appearing in new DoD contract solicitations on November 10, 2025. The CMMC requirement date timeline allows for self-attestation in the first phase, with Level 2 certifications required in subsequent contract awards based on program manager discretion. DoD estimates roughly 80,000 companies will need Level 2 certification and 1,500 will require Level 3. The CMMC requirement date implementation includes stricter POA&M closure requirements within six months, and contractors must provide annual NIST 800-171 compliance affirmations. Understanding the CMMC requirement date codification ensures defense contractors meet all regulatory obligations.
What is a CMMC RPO and is Ridge IT an RPO?
A CMMC Registered Provider Organization (RPO) is a company authorized by the CMMC Accreditation Body to provide consulting services for organizations seeking CMMC certification. Yes, Ridge IT is a certified RPO, which means we're authorized to help defense contractors navigate the complexities of CMMC compliance. Unlike typical consultants, our military-grade CMMC methodology delivers both compliance and security through continuous monitoring rather than point-in-time assessments. Ready to start your certification journey? Our RPO services include gap analysis, remediation planning, and implementation support with our 15-minute response guarantee.
How do I meet DoD CMMC requirements?
What are the DoD CMMC compliance standards?
When do DoD CMMC requirements start?
After December 16, 2024, CMMC compliance becomes mandatory for DoD contractors. See critical timeline mistakes contractors make during implementation.
How long does CMMC Certification take?
Most organizations need 12-18 months to achieve full certification. The process includes 3-6 months implementing military-grade security controls through our proven implementation framework. Then, as outlined in our maturity requirements guide, you must demonstrate these practices are embedded in your culture - typically requiring 3-6 months of documented operational evidence. Only then can you begin the formal assessment process.
Can I meet CMMC security requirements with my current IT team?
Most internal IT teams lack the specialized expertise for CMMC security controls. Our managed IT brings proven security control frameworks that map directly to certification requirements. While basic security tools focus on alerts, we prevent breaches through automated remediation and continuous compliance validation.
How do you choose between CMMC compliance companies?
What’s the CMMC rollout schedule after the Final Rule?
The rollout begins immediately after the Final Rule takes effect December 16, 2024. Our managed IT helps you stay ahead of key milestones through automated compliance monitoring. The acquisition rule (48 CFR Part 204) is finalized, published, and will take effect November 10, 2025. If your organization handles Federal Contract Information (FCI) or Controlled Unclassified Information (CUI), the compliance countdown has officially begun. Most contractors need 12-18 months for certification, so waiting risks contract eligibility.
Do subcontractors need CMMC Certification?
Yes, but our unique approach can help. While flow-down typically requires matching certification levels, our subcontractor compliance guide explains how our Zero Trust architecture can eliminate this requirement.
How does CMMC affect my existing NIST compliance?
CMMC enforces NIST SP 800-171 and 800-172 requirements through verification. Review our NIST compliance guide and see how our Zero Trust architecture streamlines both frameworks.
What’s the real difference between CMMC 1.0 and CMMC 2.0?
While CMMC 2.0 reduces levels from five to three, it demands more sophisticated controls than ISO 27001 or HIPAA. See the complete version comparison and learn how our military-grade implementation addresses these elevated requirements.
How are CMMC assessments different from self-certification?
Third-party CMMC assessments are now mandatory because self-certification proved unreliable - DoD audits found only 10-15% compliance. Review our assessment requirements guide and learn how our C3PAO certification process ensures compliance.
What happens if you miss the CMMC deadline?
After the Final Rule takes effect December 16, 2024, non-certified contractors lose DoD contracts immediately. Our military-grade compliance solutions ensure you maintain contract eligibility.
Will CMMC requirements be delayed?
No. The Final Rule is published and deadlines are set for 2025. Defense contractors now have exactly 60 days until CMMC requirements begin appearing in new DoD contract solicitations on November 10, 2025.
Can I self certify for CMMC?
Self-certification is only available for CMMC Level 1 and requires annual renewal with a senior official affirmation. Our certification requirements guide explains why Level 2 requires third-party assessment from an authorized C3PAO assessor, while Level 3 mandates direct government evaluation. The DoD implemented these stricter requirements after finding only 10-15% of self-assessed companies actually met compliance standards.





