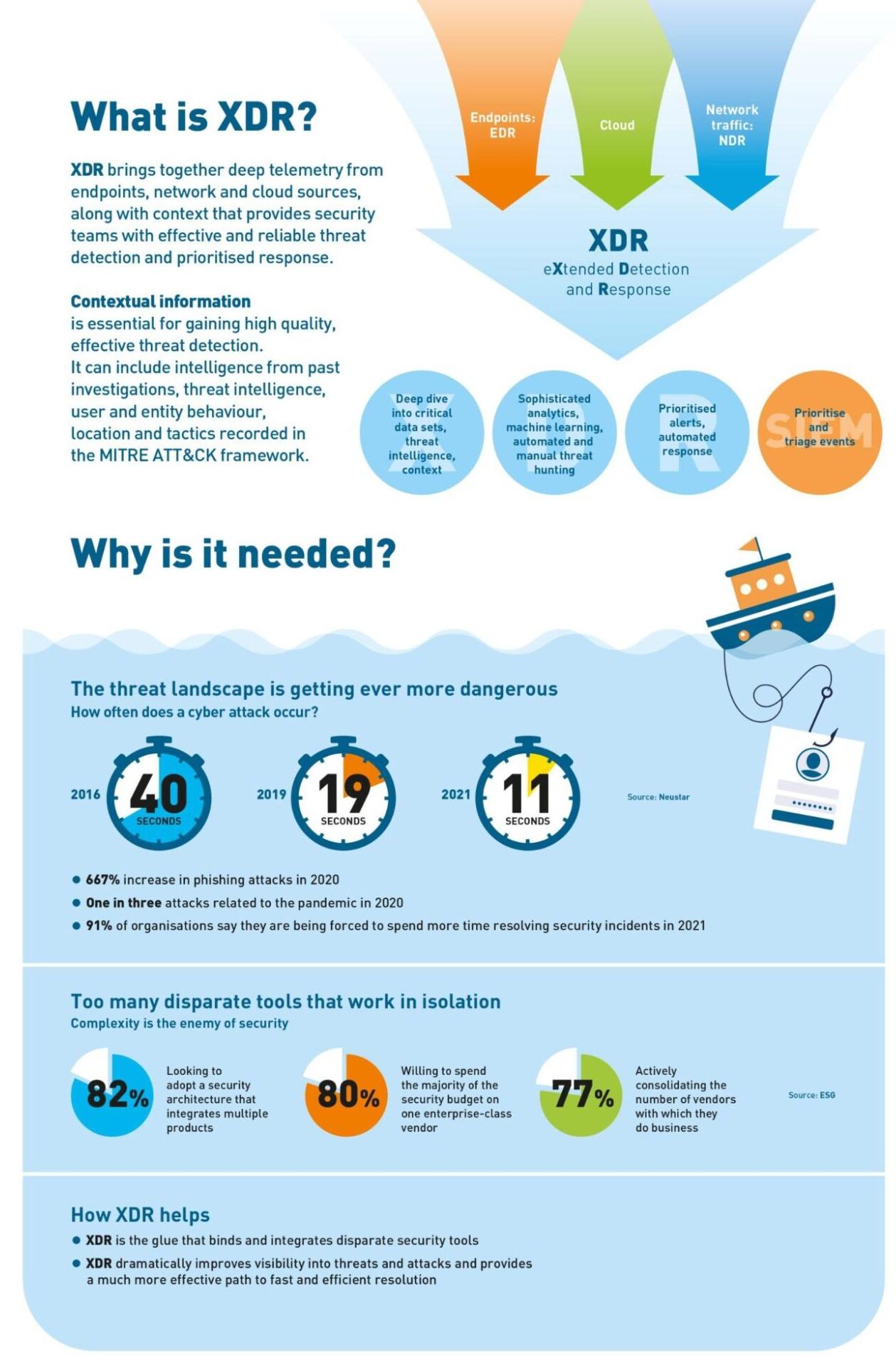
Cyber threats are becoming more sophisticated, and traditional security solutions often struggle to keep up. That’s where Extended Detection and Response (XDR) comes in. Yet what is XDR?
“Three in four companies in the U.S. are at risk of a cyberattack. XDR takes threat detection to the next level by unifying data from multiple security layers—email, endpoints, servers, cloud workloads, and networks—into a single platform. This not only speeds up threat detection but also streamlines investigation and response,” said Chad Koslow, CEO, Ridge IT Cyber.
In this blog post, we’ll go into the nuances of how XDR security works, why more enterprises are relying on XDR, the differences between XDR and other security solutions, and how our ONE Platform solution can make managing cybersecurity even easier.
What is XDR?
XDR (Extended Detection and Response) breaks down security silos by integrating data from multiple tools into one unified platform. Instead of relying on separate systems, XDR gathers threat data from endpoints, cloud workloads, email, and network activity, allowing security teams to detect and respond to threats faster.
By centralizing all this information, XDR means the enabling of faster investigation and action, giving security teams the ability to hunt down and eliminate threats across multiple domains from a single console. It offers a more complete view of your environment—making it easier to defend against sophisticated attacks and respond efficiently.
How Does XDR Work?
XDR breaks down security barriers by connecting and analyzing data across your entire IT environment. As mentioned earlier, it brings together data from multiple locations in your system such as endpoints, cloud services, email, networks, and more. XDR provides a unified view to spot threats faster.
Here’s how it works:
Collecting Data Across Security Layers
XDR starts by gathering data from every corner of your environment. It pulls in and consolidates information gathered from various regions of your system. This data could include anything from log files to user activity, ensuring that no potential threat goes unnoticed.
Normalizing and Enriching Data
Once the data is collected, XDR cleans it up, putting everything into a consistent format. It also enriches the data with additional context, which is essential for spotting real threats and reducing false positives.
Correlating Data and Running Advanced Analytics
Next, XDR connects the dots by analyzing all that data with AI and machine learning. It looks for patterns, anomalies, and suspicious behavior across the entire security landscape. By correlating data from multiple sources, XDR creates a comprehensive view of potential threats.
Building Unified Attack Stories
When XDR detects a threat, it doesn’t just show you isolated incidents. Instead, it creates a “unified attack story” that shows how various data points and events are connected. This enables XDR to identify both well-known threats and sophisticated attacks that would typically slip through traditional tools.
Investigating and Responding to Threats
Once a threat is confirmed, XDR gives security teams the tools they need to act fast. Whether it’s isolating compromised systems or blocking malicious traffic, XDR automates responses while also offering detailed insights to guide further investigation. This empowers security teams to make quick, informed decisions to neutralize threats before they spread.
This integrated approach gives you better visibility across all security domains, reducing the time needed to detect, investigate, and respond to attacks.
Source: Bloor Research
The Benefits of XDR: Why More Enterprises Are Relying on This Future-Facing Cybersecurity Solution
As cyber threats continue to evolve, more enterprises are adopting XDR to stay ahead of attackers. Here’s why.
Reduced Workload Through Automation
XDR lightens the load on security teams by automating routine tasks, allowing analysts to focus on more complex threats. This reduces burnout and maximizes team efficiency while addressing more advanced threats quickly.
Enhanced Visibility Across Your Entire Environment
XDR brings together data from endpoints, networks, cloud services, and identity management, giving businesses complete visibility across all layers of their infrastructure. This holistic view helps detect and stop attacks that would otherwise remain hidden in siloed systems.
Growing Network Complexity
With many companies using dozens of security tools, managing them has become overwhelming. XDR simplifies security operations by unifying all your security data, making it easier to spot and respond to threats quickly and effectively, eliminating the blind spots attackers exploit.
Faster Threat Detection and Response
XDR’s AI-driven threat detection and response drastically cuts down on the time it takes to spot and neutralize cyberattacks. By correlating data from various domains, XDR provides your team with a complete attack story, reducing noise from false positives and speeding up response times.
Reducing the Cost of Data Breaches
With the average cost of a data breach hitting $4.45 million in 2023, XDR helps lower the financial impact by detecting attacks faster, reducing the time attackers can remain undetected. This shortened dwell time reduces business disruptions and minimizes the overall cost of a breach, making XDR a key tool in mitigating financial losses.
|
Learn more about your cybersecurity options: |
The Differences Between XDR and Other Security Solutions
XDR in cybersecurity offers a comprehensive approach to threat detection and response, extending protection across multiple layers of your IT environment.
EDR (Endpoint Detection and Response) focuses exclusively on monitoring end-user devices like laptops, phones, and tablets. It detects threats that traditional antivirus tools miss but is limited to endpoint data. While EDR is essential for protecting devices, it doesn’t offer the full visibility needed for modern, complex environments.
NDR (Network Detection and Response) specializes in monitoring network traffic. It detects hidden threats by analyzing communications across on-premises, cloud, and hybrid environments. However, NDR focuses solely on network data, leaving endpoints, email, and cloud workloads out of the equation.
XDR (Extended Detection and Response) goes beyond both EDR and NDR by unifying data from endpoints, networks, cloud workloads, servers, email, and more.
It gives you a holistic view of your entire infrastructure, breaking down the silos that other solutions often create. This broader coverage means XDR detects advanced threats that would otherwise go unnoticed in isolated systems, enabling faster, coordinated responses across your organization.
With XDR, you’re securing everything from devices to the cloud in one streamlined platform. This not only improves threat detection but also accelerates investigation and response, making your cybersecurity operations more efficient and effective.
While XDR provides a comprehensive approach to unifying and enhancing threat detection across your IT environment, Ridge IT Cyber’s ONE Platform takes this even further by simplifying security management.
Strengthen Your Security with Ridge IT Cyber’s CrowdStrike Certified Falcon Administrators
Protect your business with Ridge IT Cyber’s advanced XDR solutions.
Our proactive approach focuses on preventing attacks before they happen, with a highly skilled team of CrowdStrike Certified Falcon Administrators (CCFA) ready to respond to threats quickly and effectively.
Using industry-leading solutions like CrowdStrike and Zscaler, we provide multi-layer security that detects threats early, contains them, and prevents lateral spread. Stay ahead of evolving cyber threats with real-time monitoring, cloud-based updates, and MITRE Framework implementation to keep your systems secure.
Contact us today to learn more.








